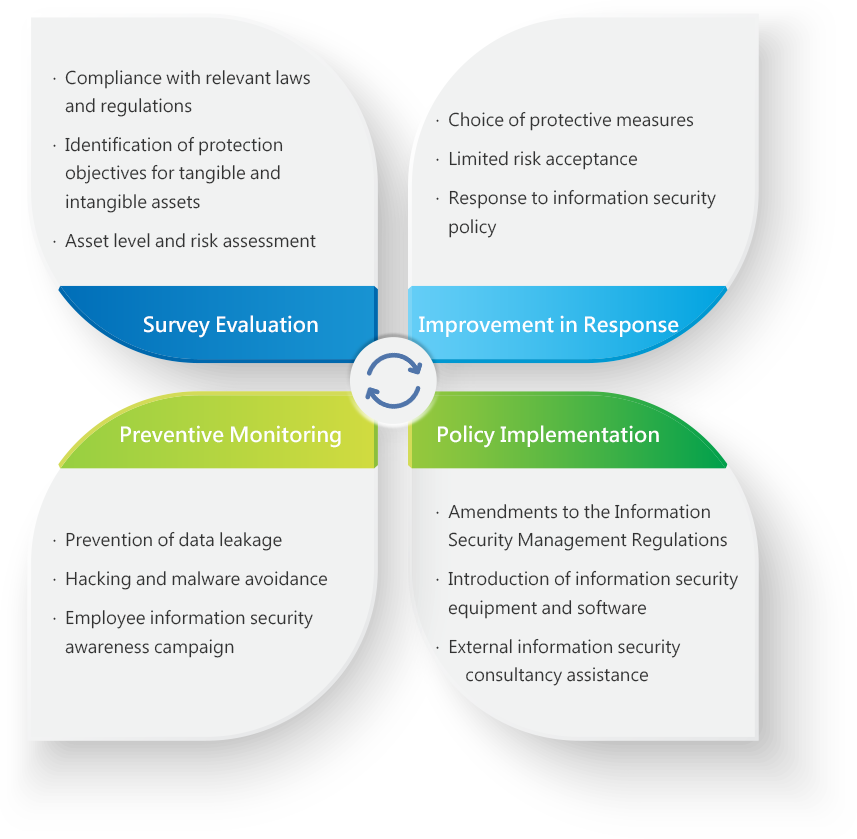
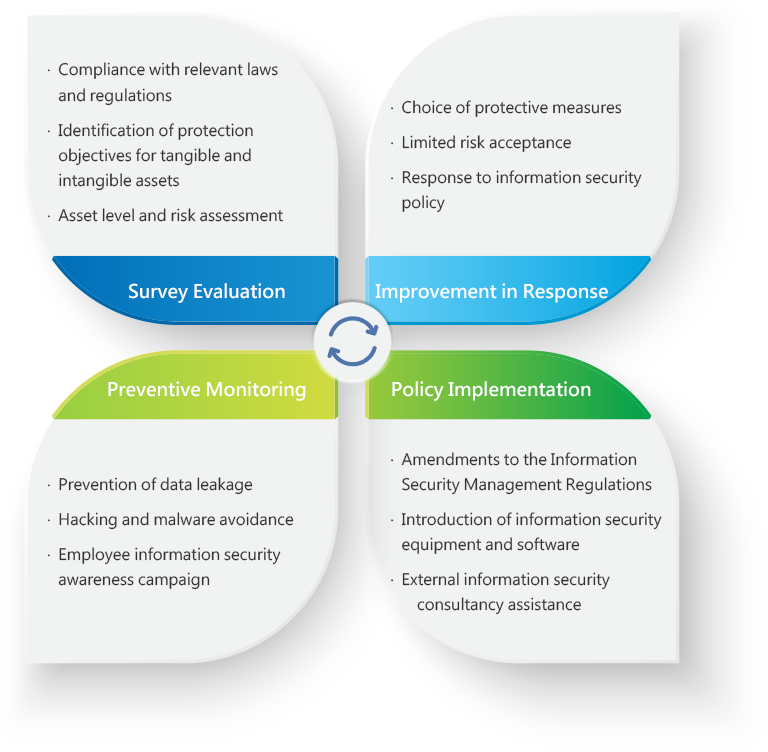
Information Security Risk Management Framework
- The Company’s Information Management Section in charge of information security is responsible for planning, implementing and promoting information security management, and heightening information security awareness.
- If any deficiencies are found, the Company’s Auditing Office, as an information security audit unit, will immediately request the audited unit to come up with relevant improvement plans and regularly track the effectiveness of the improvement to reduce the internal information security risk.
- The results of the information risk assessment shall be submitted to the responsible supervisor for approval.
Information Risk Management Cycle
Information Security Policy
Our Company adheres to the corporate mission and philosophy of integrity and sustainable operation, and hereby promulgates this information security management policy to ensure that the internal information systems of the Company maintain effective operation, preserve confidentiality, integrity and availability.
This policy aims to provide employees with a clear guiding principle in their daily work, and all employees are obliged to actively participate in the promotion of information security management policy to ensure the safe operation and maintenance of all employees, data, information systems, equipment and network of the Company, with the hope that all employees can understand, implement and maintain it to achieve the goal of sustainable information operations.
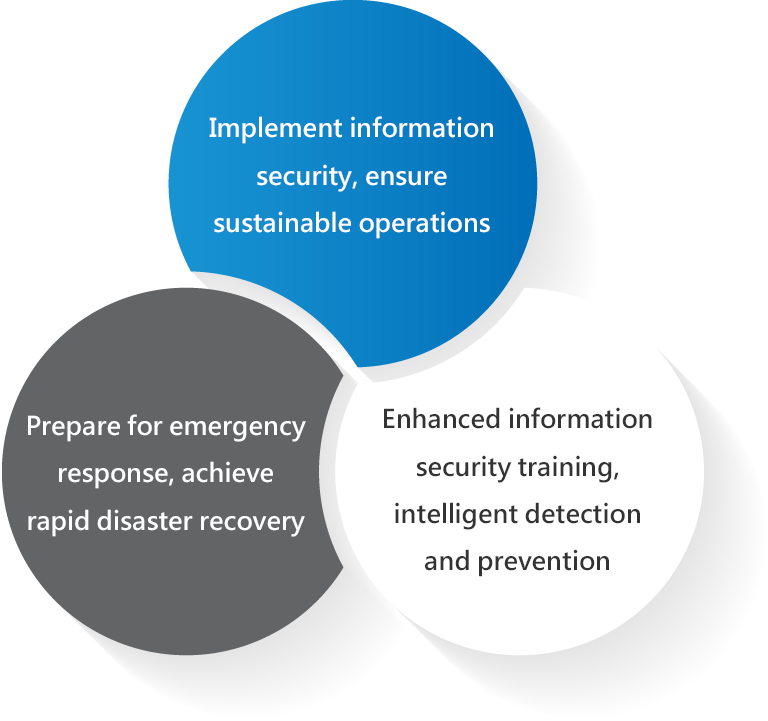
Current Implementation
Current Implementation
- ‧ Enhanced computer access management
- ‧ Account privilege inventory
- ‧ Off-site data backup
- ‧ High availability master system architecture
- ‧ Regular information security audit mechanism
- ‧ Implementing recovery drills
- ‧ DRM file protection software
Medium- to Long-term Goals
Medium- to Long-term Goals
- ‧ Introduction of endpoint protection
- ‧ Behavior track record
- ‧ Regular enhancement of employee information security awareness
- ‧ Intelligent intrusion detection and prevention
- ‧ Data transmission traffic monitoring
- ‧ Cross-border off-site data backup
- ‧ Social software restrictions and monitoring
Information Security Management System, ISMS Implementation
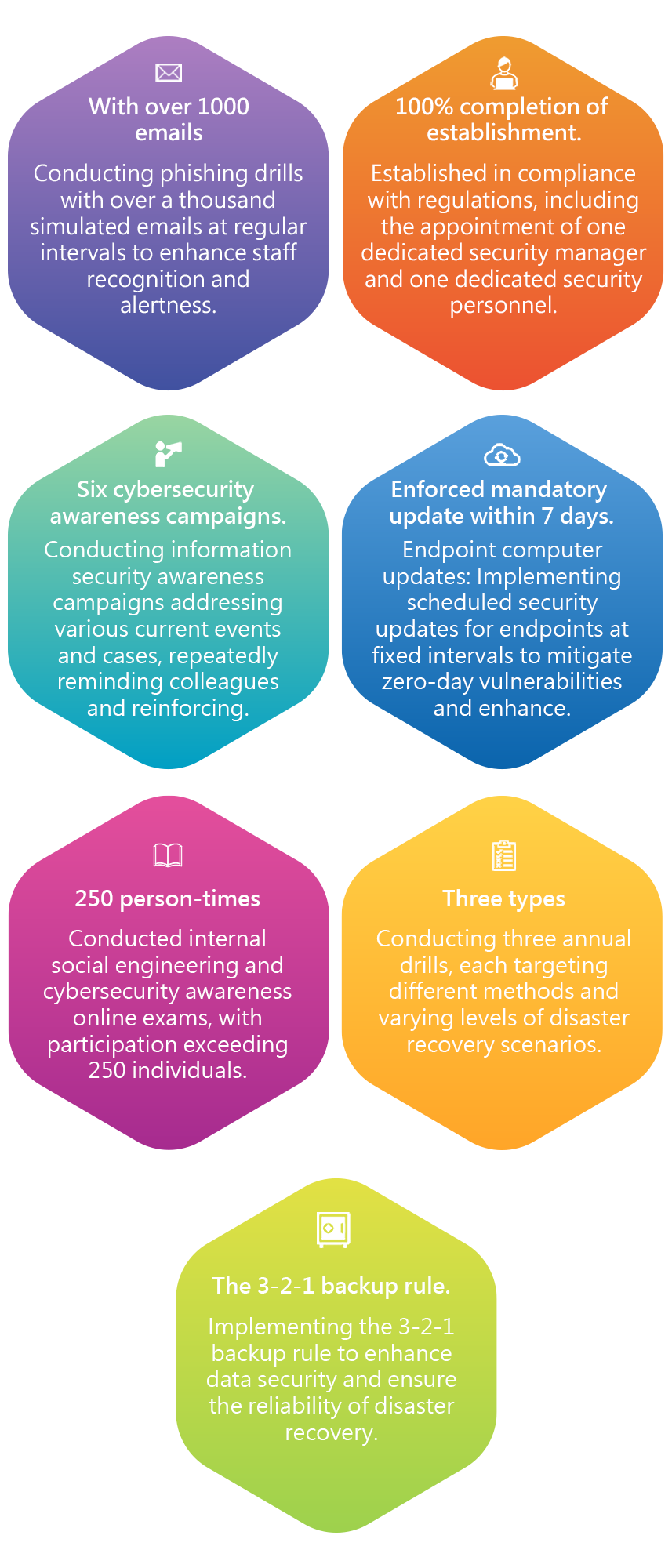
In recent years, the greatest risk to information services has emerged from the widespread proliferation of ransomware, fueled by the rise of cryptocurrencies.
To address such attacks, the company has implemented ISMS on both the endpoint device and Server-side systems:. On the endpoint device, regular users' devices are equipped with antivirus and anti-intrusion software for protection. There is a requirement for crucial operational information to be stored in the system and controlled storage areas to mitigate the risk of a single point of compromise. To enhance preventive measures related to user awareness, investments have been made in web filtering, email filtering services, and devices. Additionally, efforts have been directed towards strengthening personnel's cybersecurity awareness, conducting social engineering drills, and promoting awareness of cybersecurity incidents.
On the Server-side systems:, the company follows the 3-2-1 backup rule to ensure data resilience. Control over storage areas and the rapid recovery capability of virtual machines are maintained to enhance the overall security posture.
 English
English 日本語
日本語 繁體中文
繁體中文 簡體中文
簡體中文 Русский
Русский 韓文
韓文